
Cybersecurity in the UTM context has an expansive scope since it touches cyber-physical systems and covers different domains. The threat modelling template conceptualised by the Secure and Resilient UTM Task Force introduces a way of thinking to address the issues of cyber-security of UTM systems to build a secure-by-default UTM system. In the context of the drone ecosystem, UTM is just one component of the stack, and there are others, e.g. the vehicle itself, the command and control link, the identity and authorization of the flights, etc.
During the work of the Secure and Resilient UTM Task Force, a number of task force GUTMA members presented a short summary showcasing their work and technology that covers the broader offering in the context of cyber-secure systems. In this article, we share this “survey of practices” that will familiarize the reader with the broader work and efforts done by task force members.
This first article will focus on the contribution of the Technology Innovation Institute (TII).
Introduction
The Technology Innovation Institute (TII) is a pioneering research centre that focuses on applied research and new-age technology capabilities. The Secure Systems Research Centre (SSRC) is part of TII, focusing on Zero Trust end-to-end security and resilience in cyber-physical and autonomous systems. As a participant in the open-source UTM ecosystem, the focus is to define and promote the implementation of Zero Trust principles for secure communication between Unmanned Aircraft Systems (UAS) and UTM systems. Zero Trust is a security framework that challenges the traditional perimeter-based security approach and adopts a holistic approach to secure communication. Through our efforts in the open-source ecosystem, we seek to foster innovation, drive industry-wide adoption of secure communication practices, and enhance the overall security and resiliency of UAS operations within the UTM ecosystem.
Methodology
The cyber resiliency of a sophisticated and distributed system, such as the unmanned air traffic management system (UTMS), hinges on the robustness of its various components, including UAVs, GCS, Operators, UTMSP, and DSS. The system’s ability to withstand cyber threats is intricately connected to the resilience of these individual elements and the effectiveness of their communication links. At TII, we adopt a zero-trust approach, emphasizing a comprehensive strategy for securing our systems and networks. This strategy involves consistently verifying the identity and trustworthiness of all elements within our infrastructure, operators, ground control stations (GCS), UAVs, UTMSP, and DSS. By adhering to this approach, we bolster the cyber resiliency of our unmanned air traffic management system (UTMS).
Our security measures draw inspiration from various threat modelling approaches, ensuring a comprehensive defence strategy. Our reference approach included STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) and other industry-recognized methodologies, enhancing our proactive stance against potential cyber threats. This comprehensive perspective necessitates cybersecurity considerations across cyber-physical systems, GCS/operators, UTM service infrastructure, and data exchange. Our overarching view, depicted in Figure 1, outlines our approach to identifying threats, safeguarding assets, and implementing mitigation strategies across the entire technology stack. Recognizing that threats may be intentional or unintentional, vulnerabilities or software security flaws can arise from system design issues or software deficiencies. Addressing cyber-physical threats involves countering hardware tampering, electromagnetic interference, power supply attacks, side-channel attacks, and physical tampering. On the software front, vulnerabilities and supply chain attacks with malware injection are mitigated through techniques such as static code analysis, fuzzing tests, and stack compartmentalization.
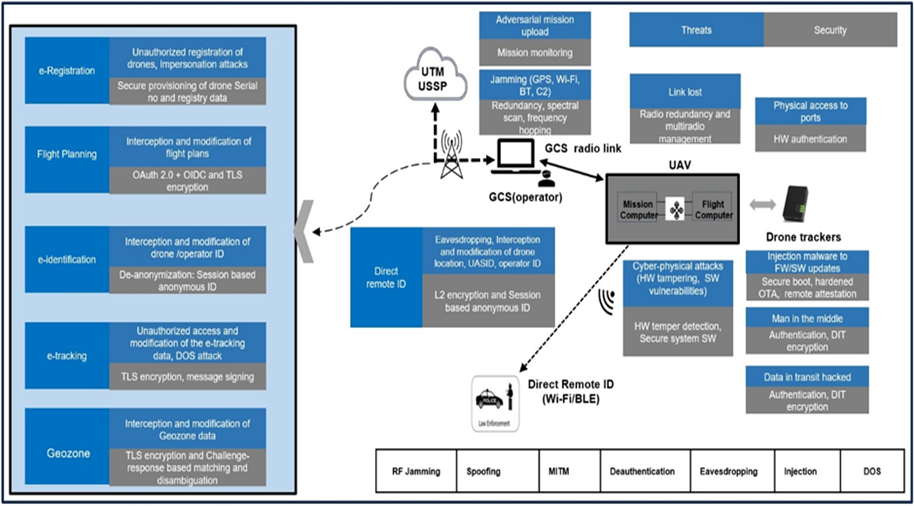
Figure 1: UTM-UAS Threat Model
Additionally, specific countermeasures are outlined for threats like jamming, spoofing, and link loss, ensuring the robustness of our systems. In the realm of cybersecurity, E-registration, e-tracking, e-identification, geozone, and traffic information services play pivotal roles in establishing secure and resilient foundations within the Unmanned Traffic Management (UTM) system.
When
employing LTE and 5G for remote identification, several vulnerabilities[1][2][3][4] impact
COTS edge devices with 5G modems. Threats depicted in Figure 2, utilizing
Software Defined Radio for cloned gNB behaviour, jeopardize UE security.
Resilience factors, such as line-of-sight paths, interference, and scattered
cell associations for drone UEs, underscore the necessity for cybersecurity
certifications in mission-critical applications[5].
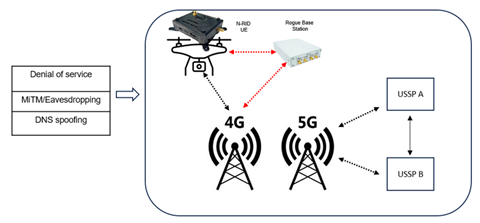
Figure 2: UTM-UAS Network Remote ID Security
Broadcasting remote ID raises privacy concerns by revealing sensitive details about both the operator and the identity of the drone, potentially compromising their privacy and security. The risks encompass cybersecurity risk, spoofing, tampering, tracking, interference, unauthorized access to data integrity, regulatory compliance, and physical security threats, as shown in Figure 3.
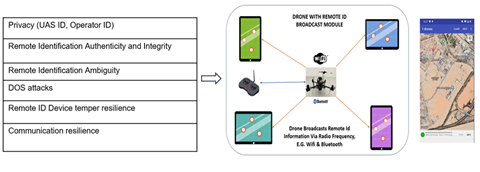
Figure 3: UTM-UAS Broadcast Remote ID Security
Conclusions
TII’s Zero Trust approach takes a holistic view by addressing security concerns across the entire ecosystem, from unmanned aerial systems (UAS) to operators, command and control (C2) communications, ground control stations (GCS), and UTM service providers. By ensuring the integrity, confidentiality, and reliability of data at every stage of transmission and storage, this comprehensive approach safeguards the secure operation of unmanned aerial vehicles, as illustrated in Figure 1.
If you want to read the full Secure and Resilient Task Force report, click here and download the document.
GUTMA Task Forces are a Members-only initiative. If you wish to become a GUTMA Member contact us at [email protected] or fill in this form.
[1] https://asset-group.github.io/disclosures/5ghoul/5ghoul.pdf
[2] https://ieeexplore.ieee.org/abstract/document/8891312
[3] https://i.blackhat.com/USA-19/Wednesday/us-19-Shupeng-All-The-4G-Modules-Could-Be-Hacked.pdf
[4] https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=10154283
[5] https://www.sesarju.eu/sites/default/files/documents/transversal/SESAR%202020%20-%20Security%20Reference%20Material%20Guidance.pdf

